이 문서는 Sonarqube-Gitlab Workflow에 Sonarscanner 작업 만들기 가이드를 공유하기 위해 작성되었다.
| 도구명 | Sonarqube, Github |
|---|---|
| 버전 | 9.5 |
| OS | CentOS 8 |
Github Self-hosted Runner 만들기
초기 서버 설정 및 설치
- 시간 확인 및 파일 읽기 수 설정
- JDK11
- NodeJS 18
- Maven 3.8.6 설치
- cmake 설치
# 시간 확인 date # 시간 서울로 변경 timedatectl list-timezones | grep Seoul sudo timedatectl set-timezone Asia/Seoul vi /etc/profile # 파일 마지막 라인에 다음 내용 입력 후 저장 ulimit -n 131072 ulimit -u 8192 # 변경된 값 확인 ulimit -n ulimit -u #JDK 11 다운로드 wget 'https://github.com/AdoptOpenJDK/openjdk11-binaries/releases/download/jdk-11.0.7%2B10/OpenJDK11U-jdk_x64_linux_hotspot_11.0.7_10.tar.gz' -O /opt/OpenJDK11U-jdk_x64_linux_hotspot_11.0.7_10.tar.gz #JDK 11 설치 cd /opt chmod 700 OpenJDK11U-jdk_x64_linux_hotspot_11.0.7_10.tar.gz tar -xvzf OpenJDK11U-jdk_x64_linux_hotspot_11.0.7_10.tar.gz mkdir java11 mv jdk-11.0.7+10/ jdk11 mv jdk11 /opt/ #적용 vi /etc/profile # 파일 마지막 라인에 다음 내용 입력 후 저장 JAVA_HOME=/opt/jdk11 PATH=$PATH:$JAVA_HOME/bin export JAVA_HOME export PATH source /etc/profile #JDK 버전 확인 echo $JAVA_HOME java -version #NodeJS 설치 sudo curl -fsSL https://rpm.nodesource.com/setup_18.x | bash - sudo yum install -y nodejs #Maven 설치 cd /opt wget https://archive.apache.org/dist/maven/maven-3/3.8.6/binaries/apache-maven-3.8.6-bin.tar.gz chmod 700 apache-maven-3.8.6-bin.tar.gz tar -xvzf apache-maven-3.8.6-bin.tar.gz ln -s apache-maven-3.8.6 maven # 파일 마지막 라인에 다음 내용 입력 후 저장 MAVEN_HOME=/opt/jdk11 PATH=$PATH:$JAVA_HOME/bin:$MAVEN_HOME/bin export JAVA_HOME MAVEN_HOME source /etc/profile #Maven 버전 확인 echo $MAVEN_HOME mvn -v #CFamily 용 설치(cmake) yum install cmake -y yum install gcc-c++
Sonarscanner 설치 및 설정
- Maven Sonarqube 설정
- Sonarscanner 다운로드
- Sonarscanner Cfamily 다운
#Maven Sonarqube 설정 추가
cd $MAVEN_HOME/conf
vim settings.xml
#해당 큰 태그에 맞춰서 해당 태그들 넣어야함(ex: PluginGroups 안에 PluginGroup)
<settings>
<pluginGroups>
<pluginGroup>org.sonarsource.scanner.maven</pluginGroup>
</pluginGroups>
<profiles>
<profile>
<id>sonar</id>
<activation>
<activeByDefault>true</activeByDefault>
</activation>
<properties>
<project.reporting.outputEncoding>UTF-8</project.reporting.outputEncoding>
<sonar.sourceEncoding>UTF-8</sonar.sourceEncoding>
</properties>
</profile>
</profiles>
</settings>
#Sonarscanner 다운로드
cd /opt
wget https://binaries.sonarsource.com/Distribution/sonar-scanner-cli/sonar-scanner-cli-4.7.0.2747-linux.zip
chmod 755 sonar-scanner-cli-4.7.0.2747-linux.zip
unzip sonar-scanner-cli-4.7.0.2747-linux.zip
#심볼릭 링크 생성
ln -s sonar-scanner-4.7.0.2747-linux/ sonar-scan
#Sonarscanner CFamily 다운로드
cd /opt/
wget {SonarQube URL}/static/cpp/build-wrapper-linux-x86.zip
chmod 755 build-wrapper-linux-x86.zip
unzip build-wrapper-linux-x86.zip
#심볼릭 링크 생성
ln -s build-wrapper-linux-x86 build-wrapper
#환경변수 등록
vi /etc/profile
# 파일 마지막 라인에 다음 내용 입력 후 저장
export SONAR_SCAN=/opt/sonar-scan
export SONAR_CSCAN=/opt/build-wrapper
#PATH에 추가
PATH=$PATH:$JAVA_HOME/bin:$MAVEN_HOME/bin:$SONAR_SCAN/bin:$SONAR_CSCAN
source /etc/profile
#확인
echo $SONAR_SCAN
echo $SONAR_CSCAN
#Runner 용 Command 설치
shasum
Github에 Self-hosted Runner 등록하기
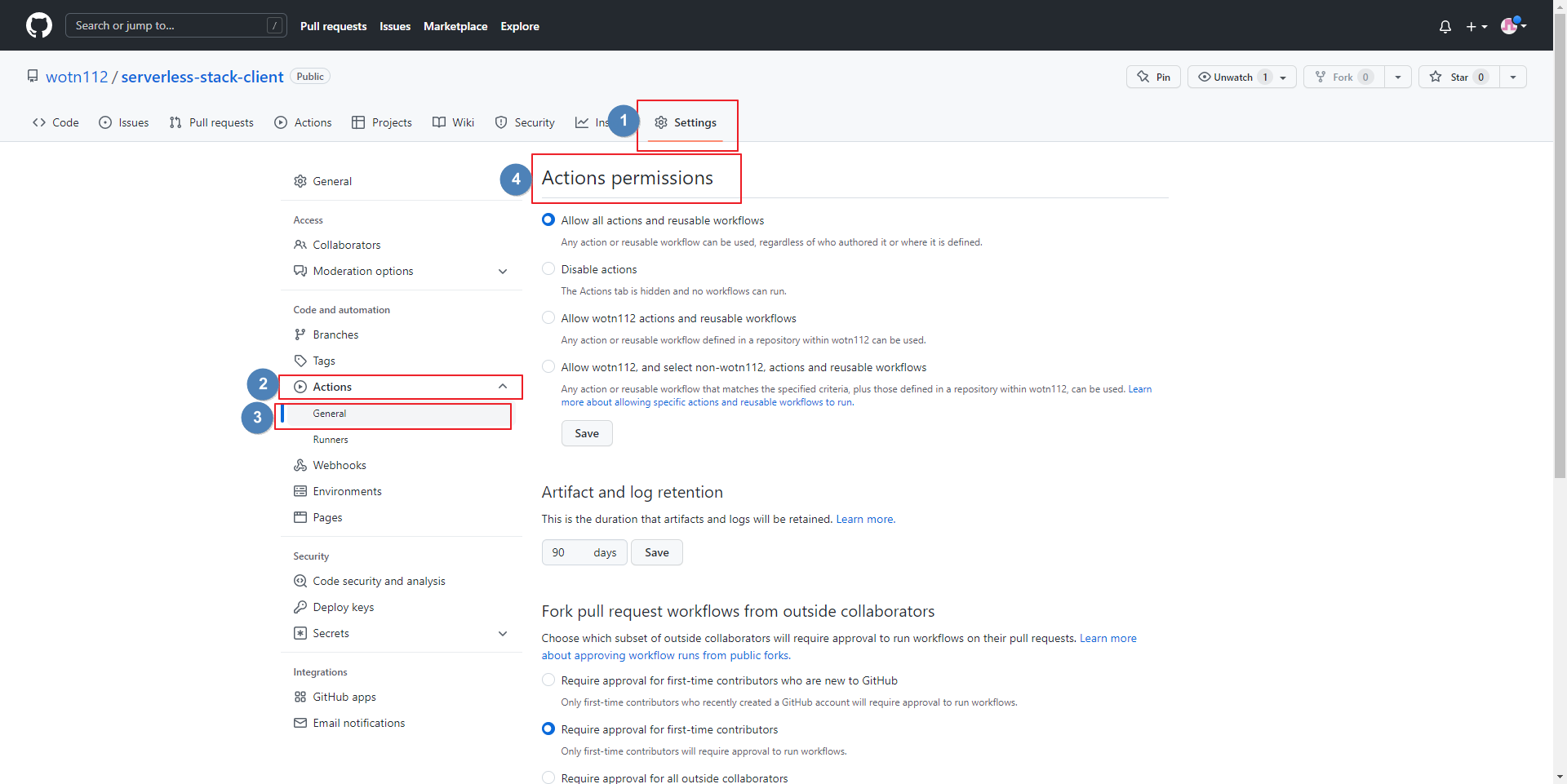
- Actions 권한 확인
Settings → Actions → General → Actions permissions
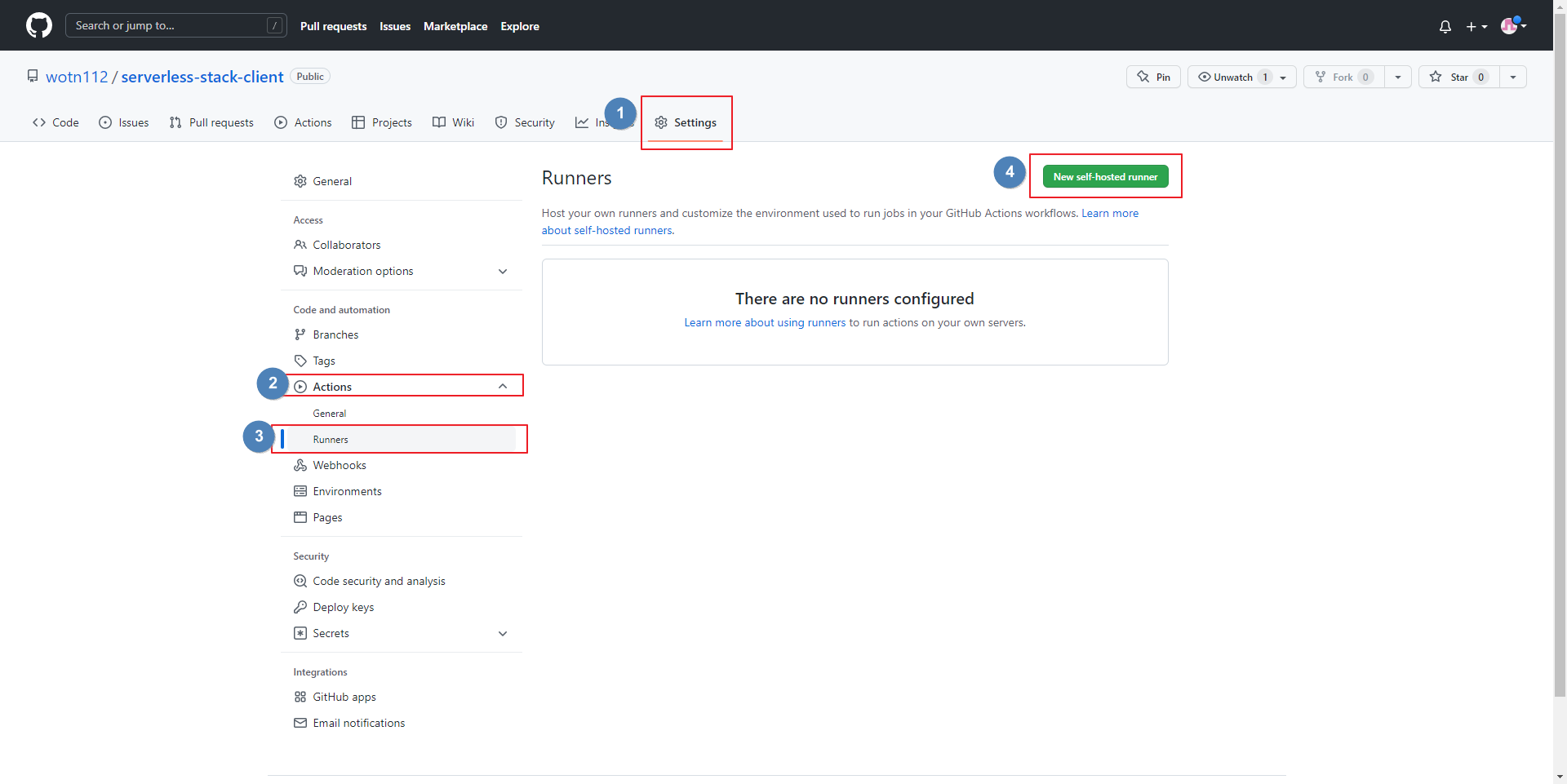
- 저장소 기준: 저장소 → Settings → Actions → Runner → New Self-hosted runner
root로 실행불가
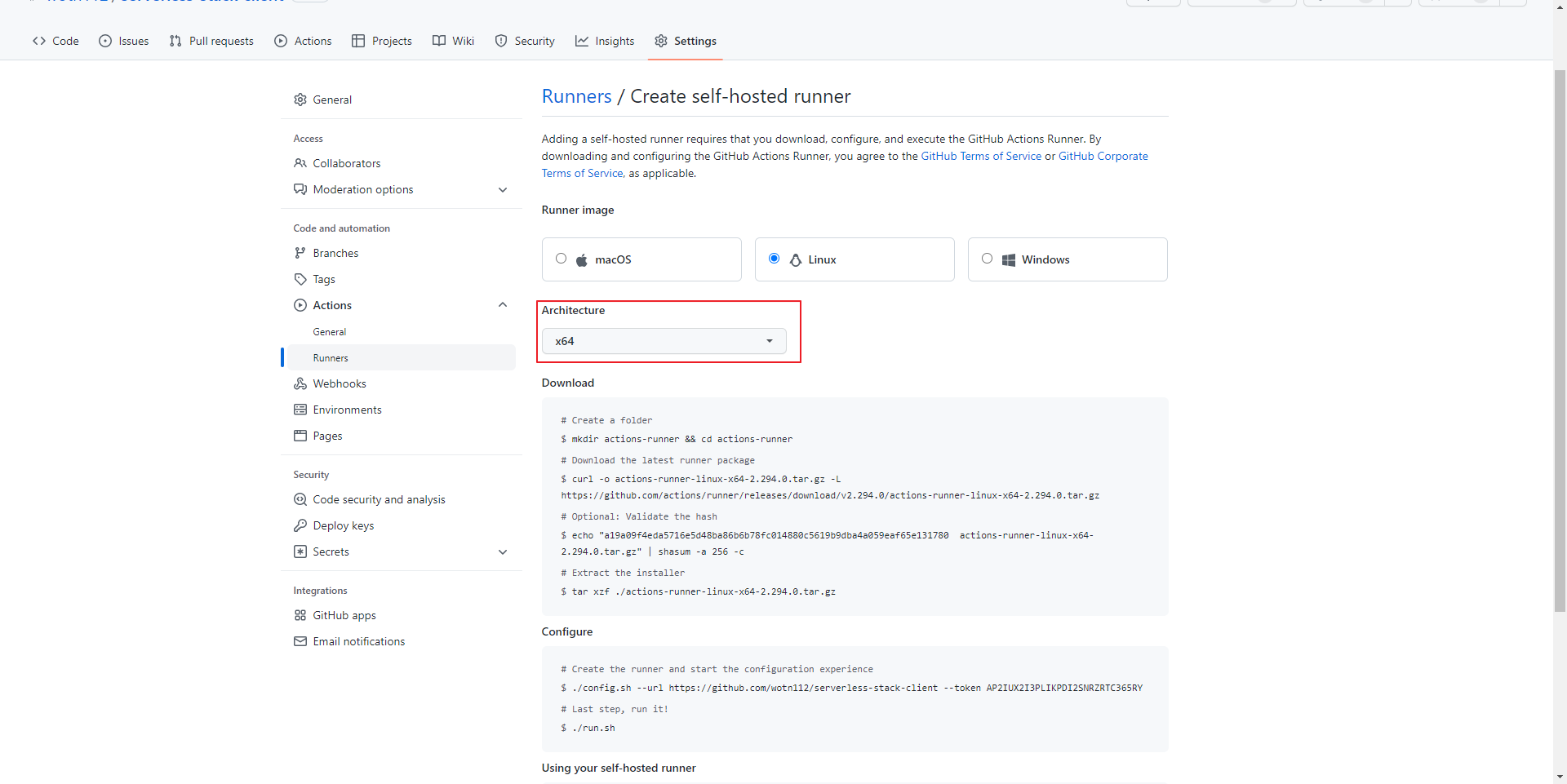
Architecture : 해당 서버에서 uname -m 으로 확인
해당 페이지에 나오는 대로 명령어 입력
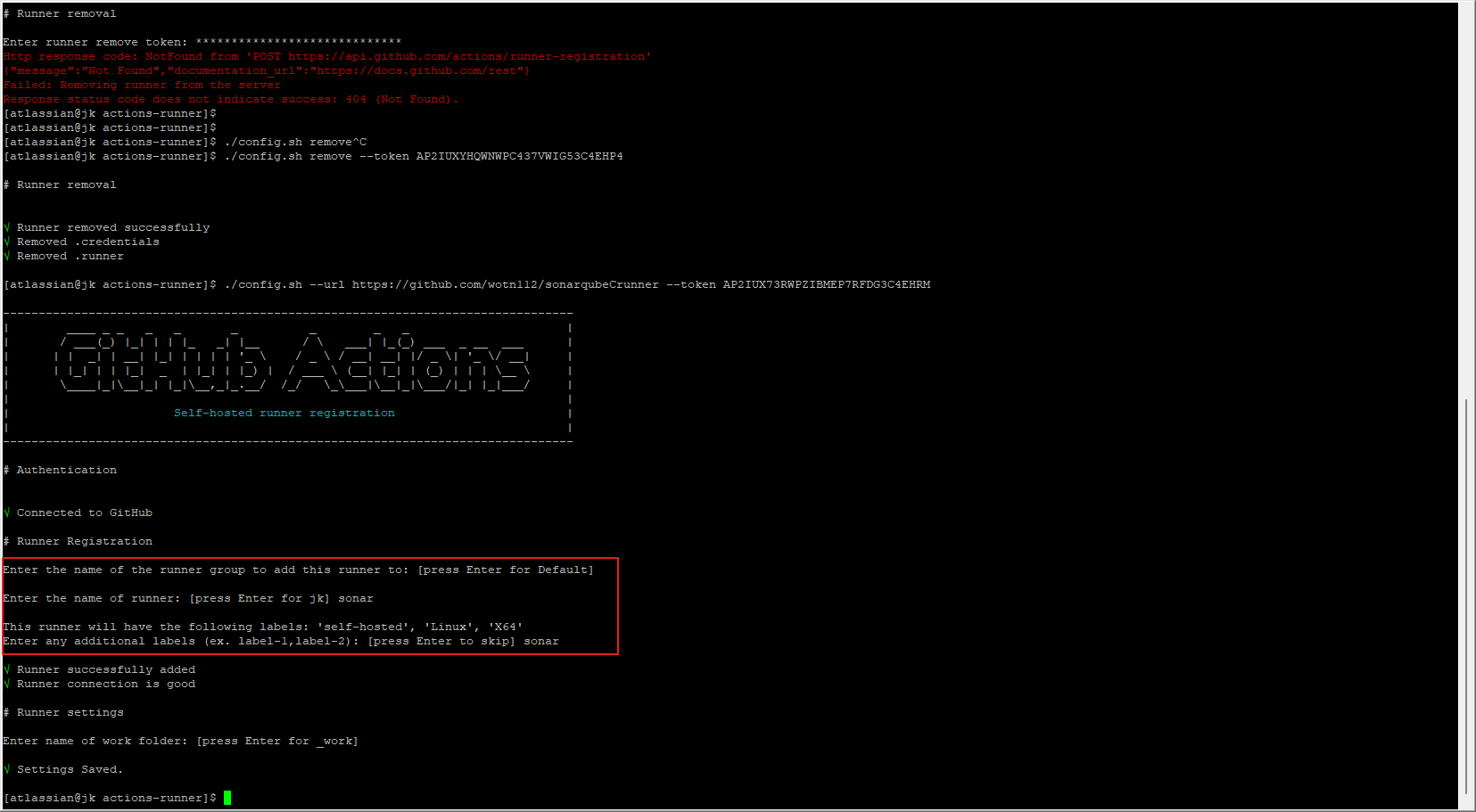
- name: sonar
label: sonar
- 해당 서버에
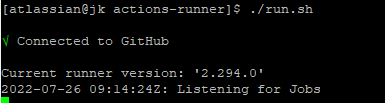
./run.sh실행(백그라운드 실행 시 "./run.sh &")서비스로 변경(
시작(sudo ./svc.sh install USERNAME)sudo ./svc.sh start)
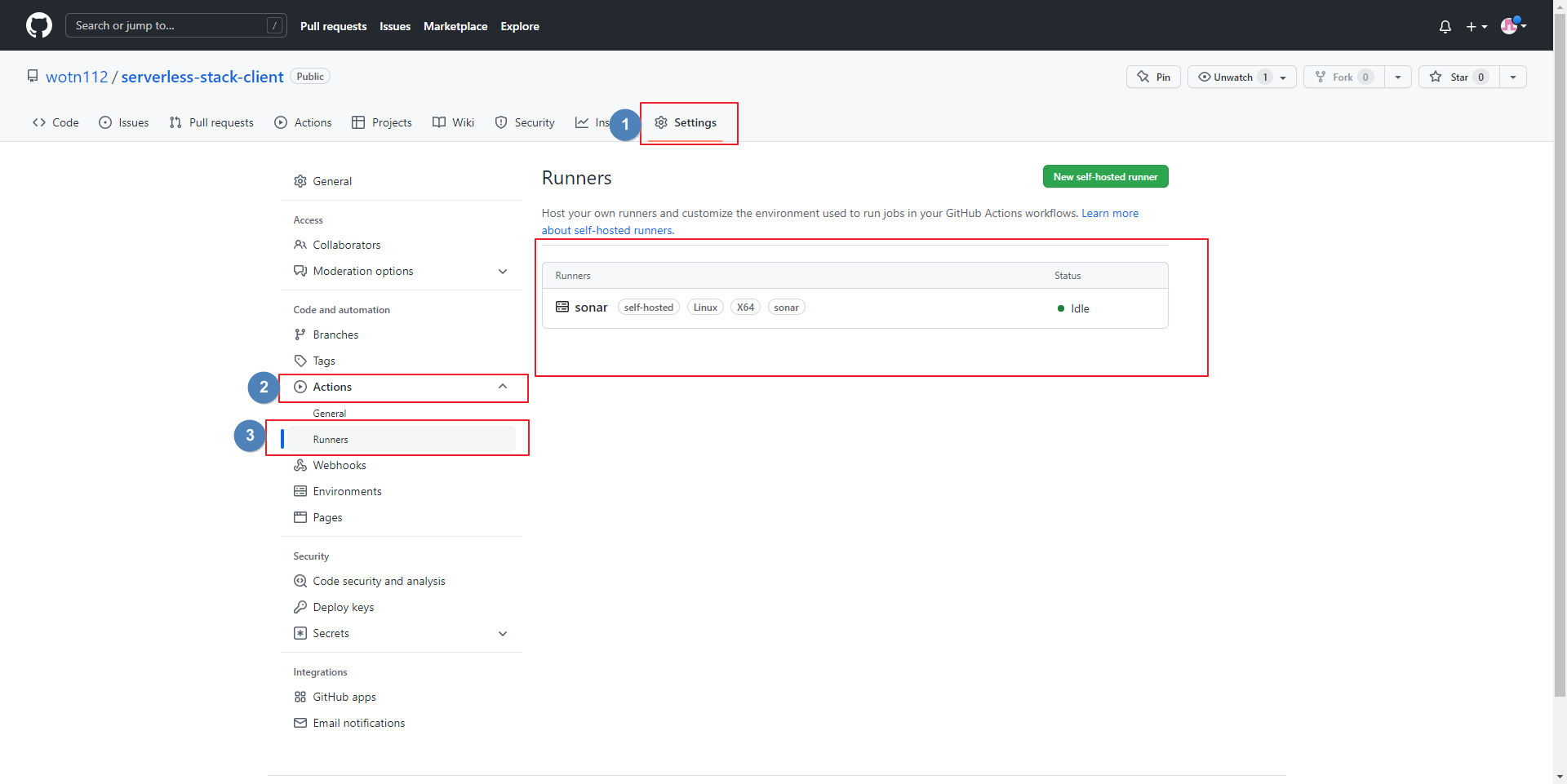
- Settings → Actions → Runners 에서 상태 확인
Github Action
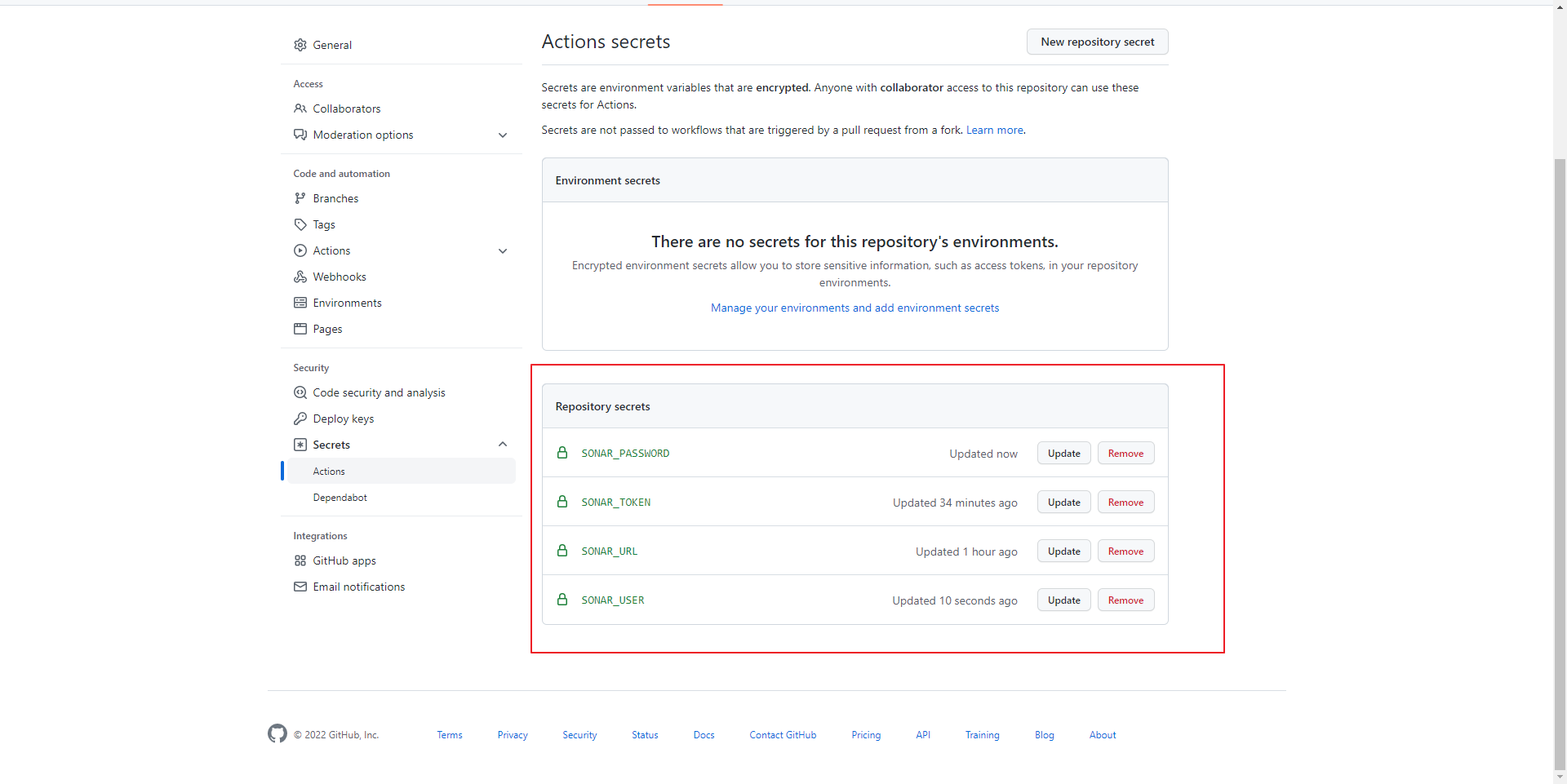
비밀키 생성하기
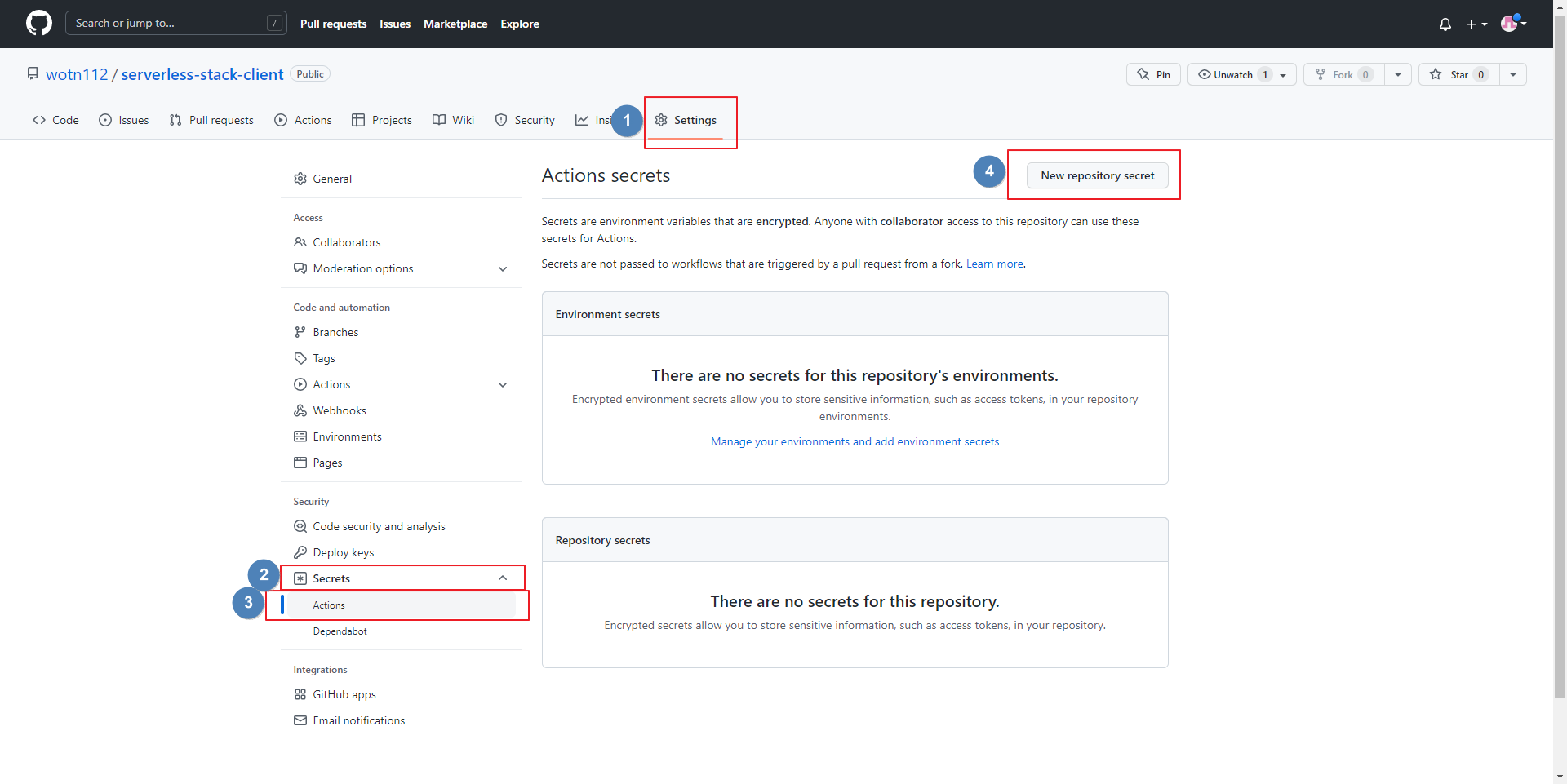
- Settings → Secrets → Actions → New repository secret 선택
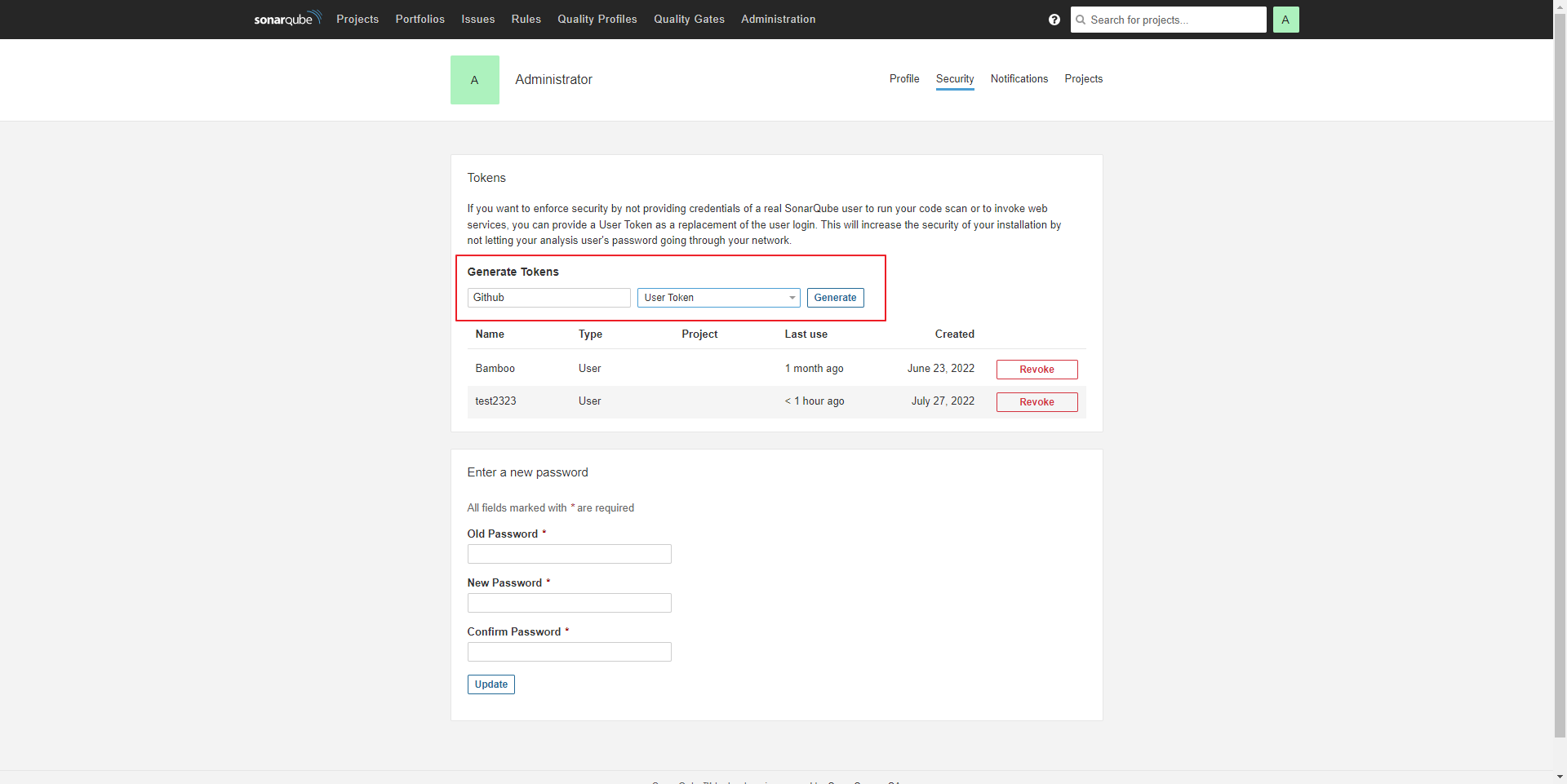
- SONAR_URL: sonarqube Url
SONAR_TOKEN: sonarqube token
SONAR_USER: sonarqube ID
SONAR_PASSWORD: 해당 ID password
Sonarqube 용 Branch 생성
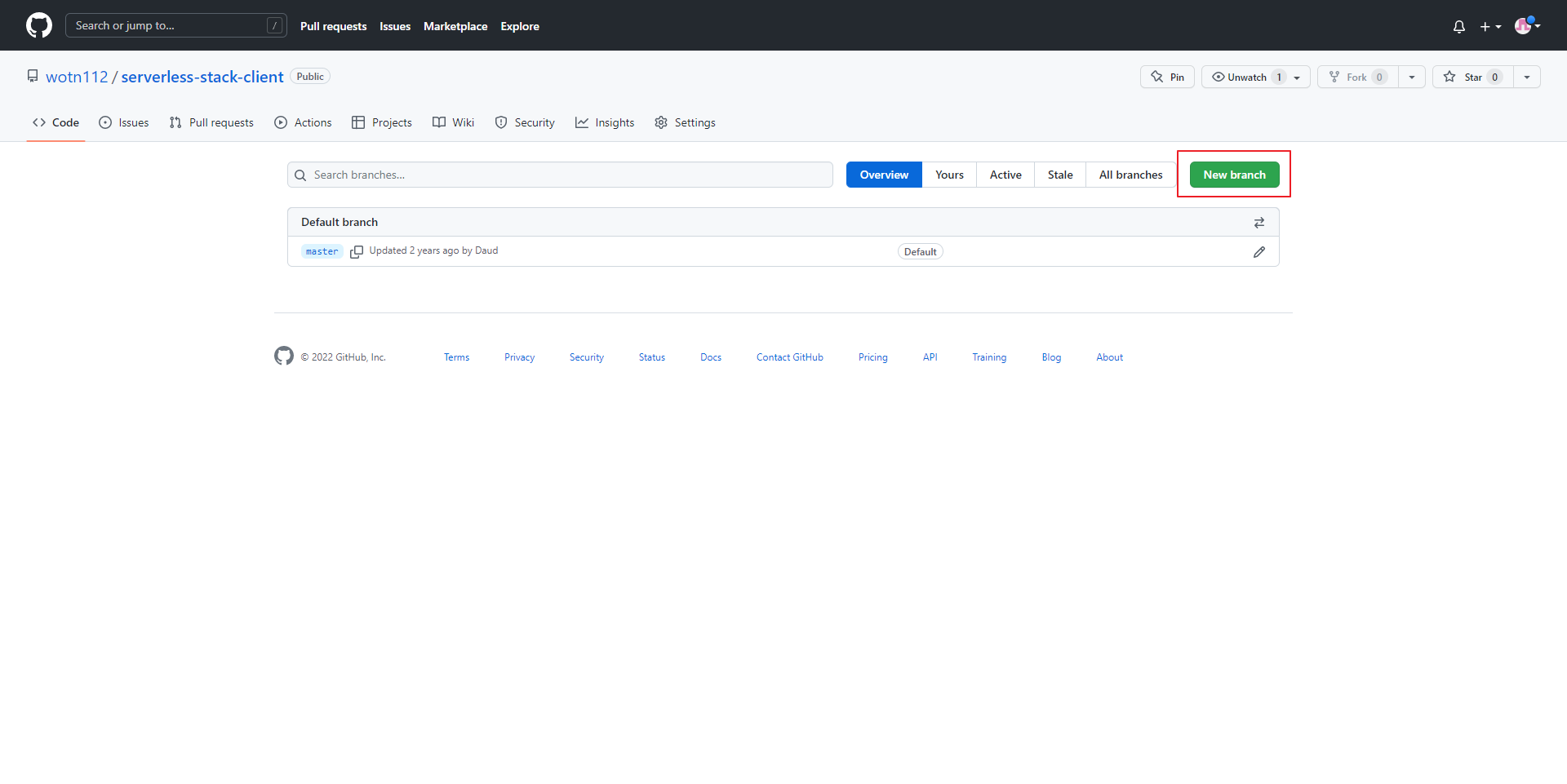
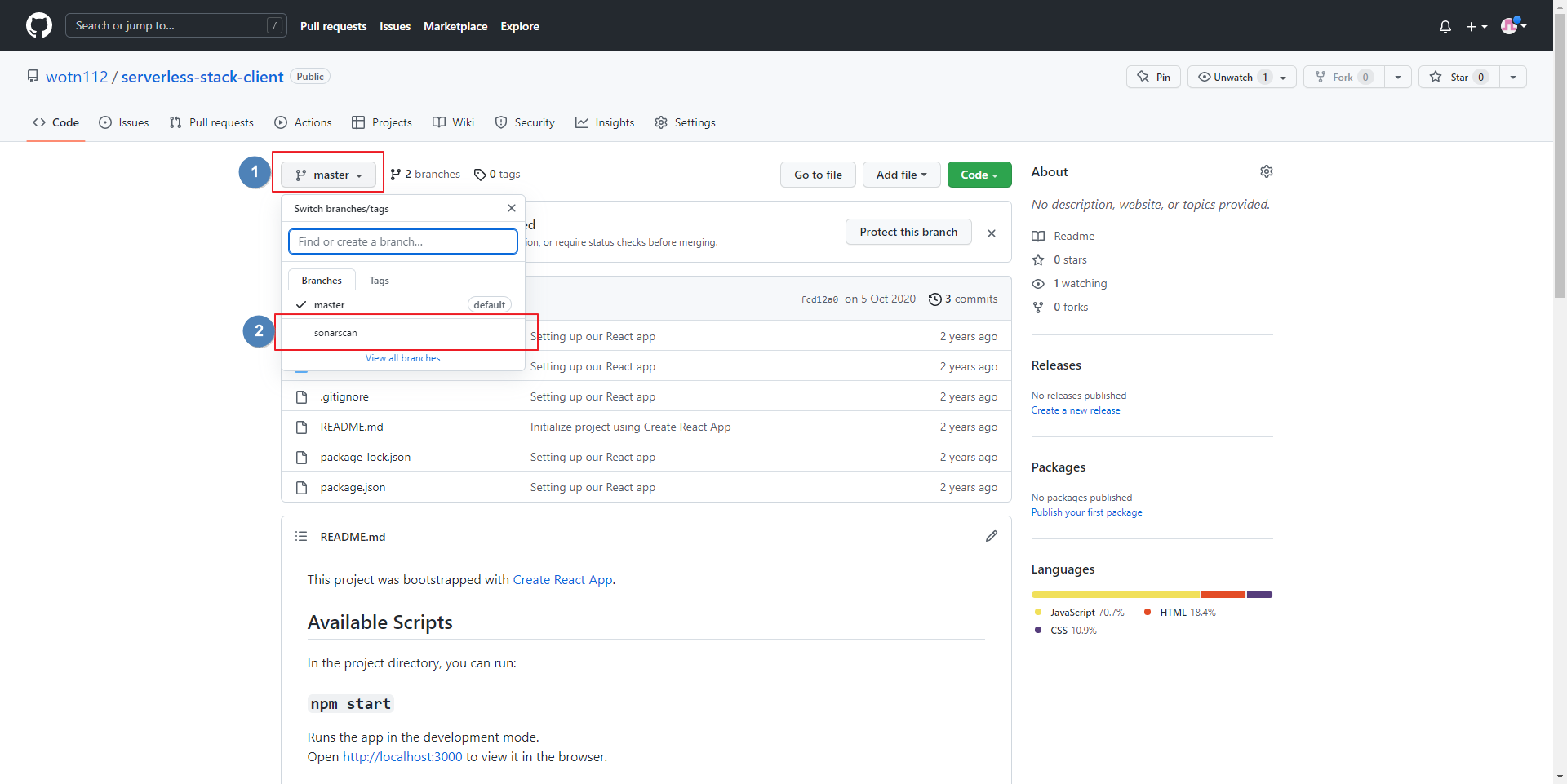
- 해당 저장소에서 branch 선택
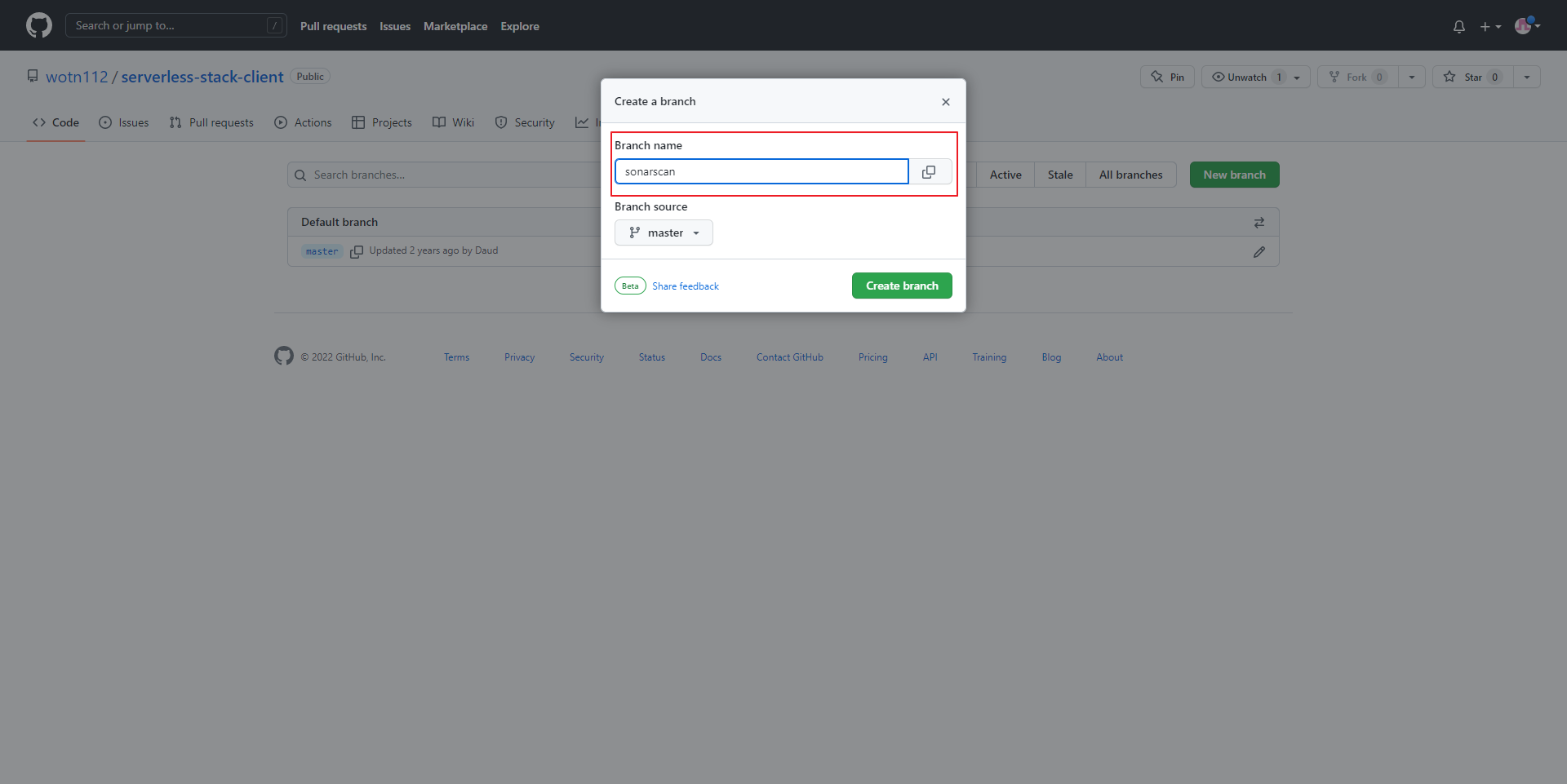
- New Branch 선택
- Branch Name: sonarscan
Workflow 생성
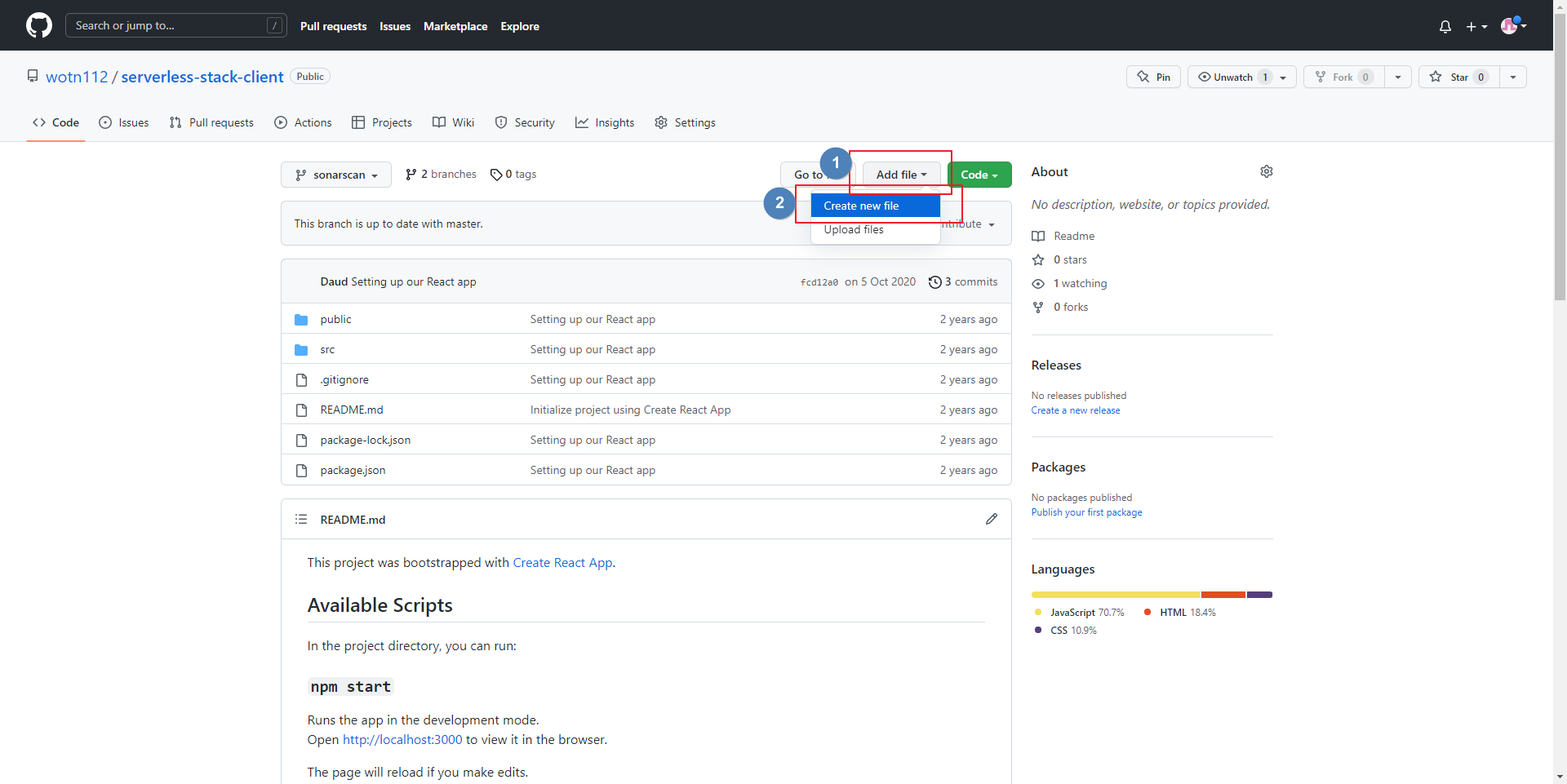
- 저장소에서 sonarscan Branch 선택
- Add File → Create New file 선택
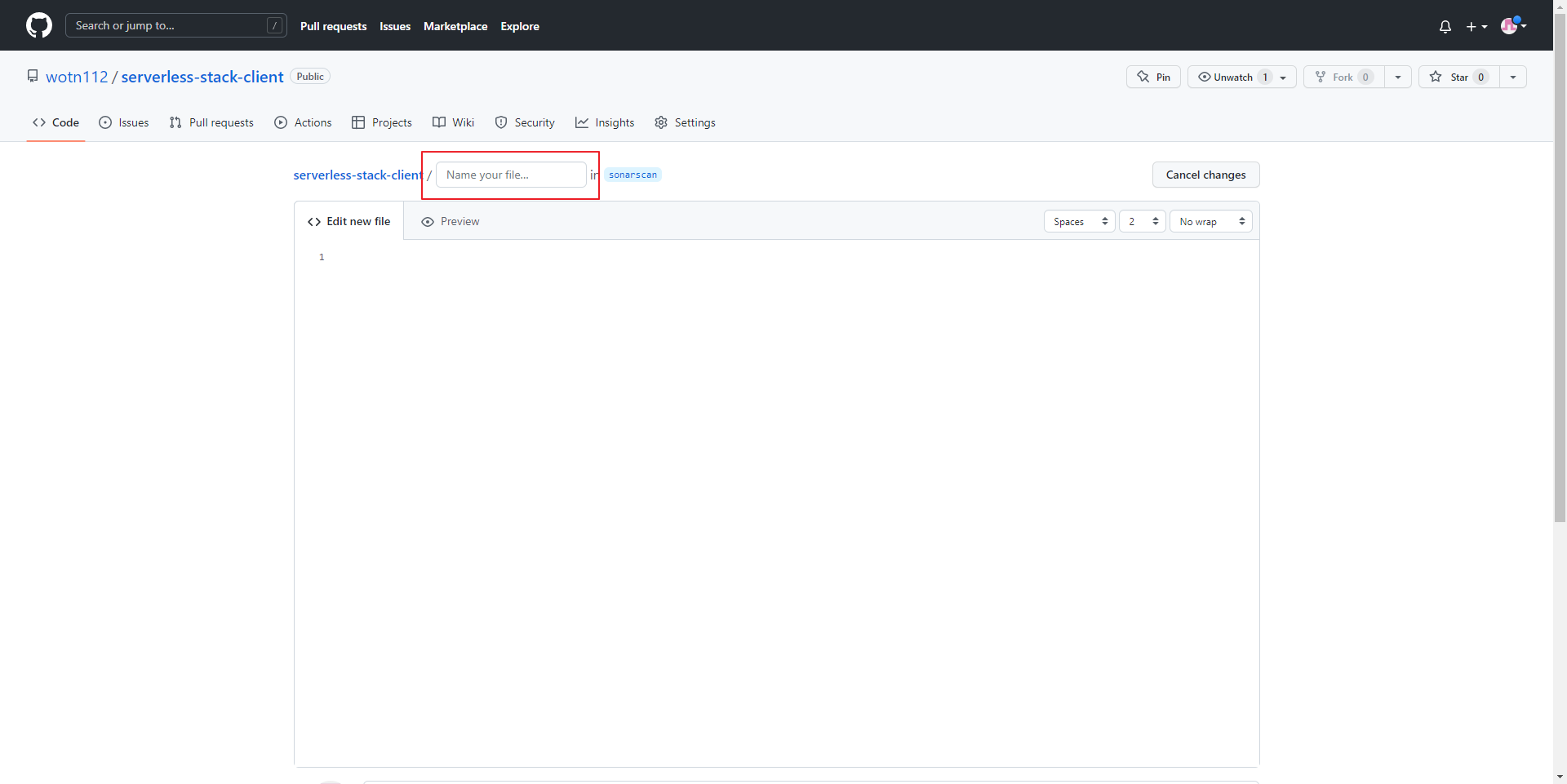
- 해당 부분에 "
/.github/workflows/sonar.yml"입력
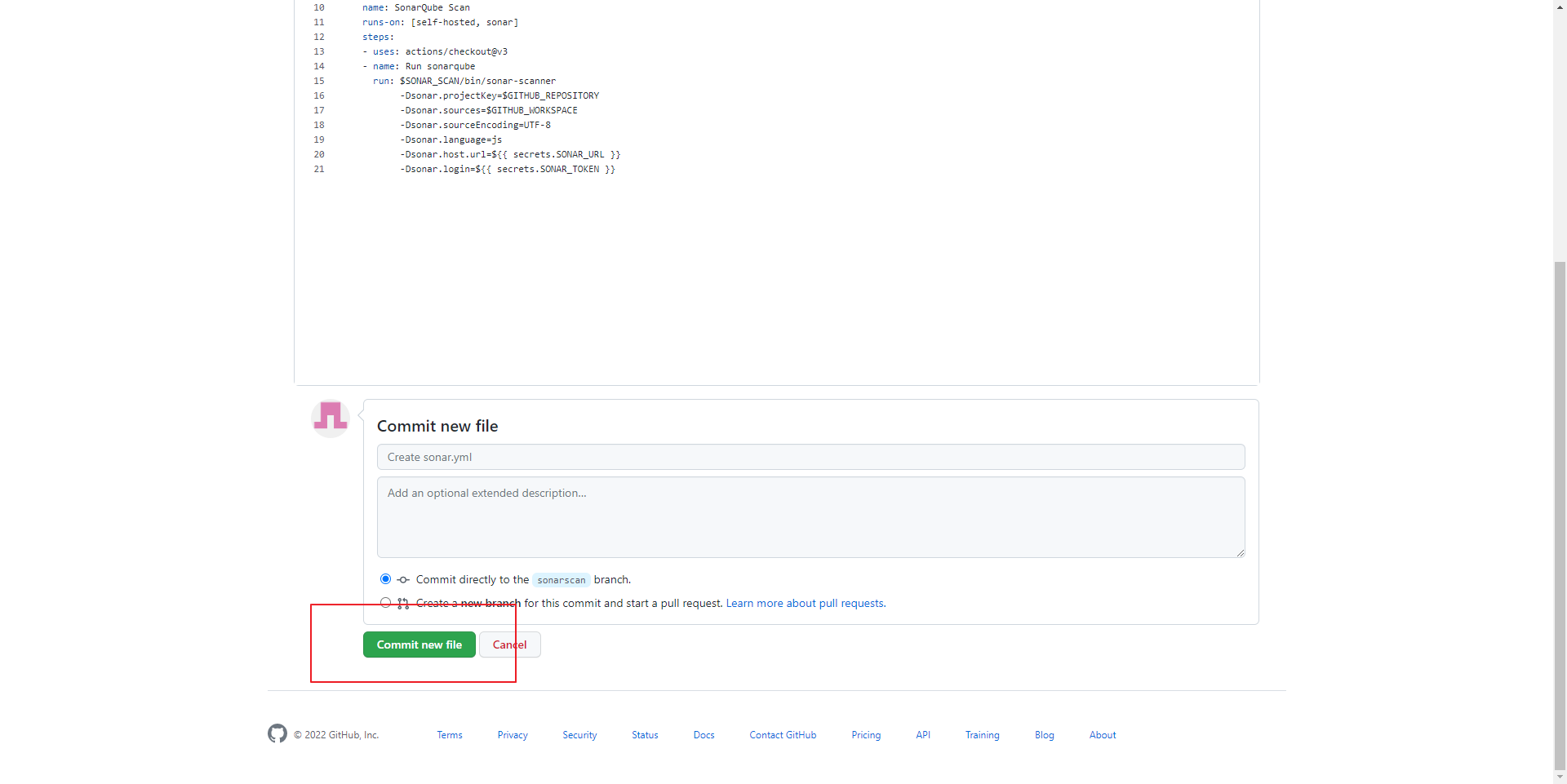
- 적용할 yml 파일 작성 후 commit new file(yml 내용은 아래 참조)
Github 자체 Runner를 통해 Sonarqube를 사용하려는 경우 Sonarqube 서버와 Github 자체 Runner 가 통신 가능해야한다
Java Maven용 Action yml 파일
- Self-hosted Runner 사용 시
on:
push:
branches:
- "sonarscan"
paths:
- ".github/workflows/sonar.yml"
name: SonarQube
env:
MAVEN_HOME: /opt/maven
SONAR_PROJECTKEY: maven
jobs:
sonarQubeTrigger:
name: SonarQube Scan
runs-on: [self-hosted, sonar]
steps:
- uses: actions/checkout@v3
- name: memory increase
run: export MAVEN_OPTS="-Xmx512m"
- name: Run sonarqube
run: $MAVEN_HOME/bin/mvn sonar:sonar
-Dsonar.host.url=${{ secrets.SONAR_URL }}
-Dsonar.login=${{ secrets.SONAR_TOKEN }}
-Dsonar.projectName=$GITHUB_REPOSITORY
-Dsonar.projectKey=$SONAR_PROJECTKEY
-Dsonar.sourceEncoding=UTF-8
- Github 제공 Runner 사용 시
on:
push:
branches:
- "sonarscan"
paths:
- ".github/workflows/sonar.yml"
name: SonarQube
env:
MAVEN_HOME: /opt/maven
SONAR_PROJECTKEY: maven
jobs:
sonarQubeTrigger:
name: SonarQube Scan
runs-on: [self-hosted, sonar]
steps:
- uses: actions/checkout@v2
with:
fetch-depth: 0 # Shallow clones should be disabled for a better relevancy of analysis
- name: Set up JDK 11
uses: actions/setup-java@v1
with:
java-version: 11
- name: Cache SonarQube packages
uses: actions/cache@v1
with:
path: ~/.sonar/cache
key: ${{ runner.os }}-sonar
restore-keys: ${{ runner.os }}-sonar
- name: Cache Maven packages
uses: actions/cache@v1
with:
path: ~/.m2
key: ${{ runner.os }}-m2-${{ hashFiles('**/pom.xml') }}
restore-keys: ${{ runner.os }}-m2
- name: Build and analyze
env:
SONAR_TOKEN: ${{ secrets.SONAR_TOKEN }}
SONAR_HOST_URL: ${{ secrets.SONAR_URL }}
run: mvn -B verify org.sonarsource.scanner.maven:sonar-maven-plugin:sonar
-Dsonar.host.url=$SONAR_HOST_URL
-Dsonar.login=$SONAR_TOKEN
-Dsonar.projectName=$GITHUB_REPOSITORY
-Dsonar.projectKey=$SONAR_PROJECTKEY
-Dsonar.sourceEncoding=UTF-8
NodeJs용 Action yml 파일
- Self-hosted Runner 사용 시
on:
push:
branches:
- "sonarscan"
paths:
- ".github/workflows/sonar.yml"
name: SonarQube
env:
SONAR_SCAN: /opt/sonar-scan
SONAR_PROJECTKEY: nodejs
jobs:
sonarQubeTrigger:
name: SonarQube Scan
runs-on: [self-hosted, sonar]
steps:
- uses: actions/checkout@v3
- name: memory increase
run: export SONAR_SCANNER_OPTS="-Xmx512m"
- name: Run sonarqube
run: $SONAR_SCAN/bin/sonar-scanner
-Dsonar.projectBaseDir="${GITHUB_WORKSPACE}/src"
-Dsonar.host.url=${{ secrets.SONAR_URL }}
-Dsonar.login=${{ secrets.SONAR_USER }}
-Dsonar.password=${{ secrets.SONAR_PASSWORD }}
-Dsonar.projectName=$GITHUB_REPOSITORY
-Dsonar.projectKey=$SONAR_PROJECTKEY
-Dsonar.sources=$GITHUB_WORKSPACE
-Dsonar.sourceEncoding=UTF-8
-Dsonar.language=js
- Github 제공 Runner 사용 시
on:
push:
branches:
- "sonarscan"
paths:
- ".github/workflows/sonar.yml"
name: SonarQube
env:
SONAR_PROJECTKEY: nodejs
jobs:
sonarQubeTrigger:
name: SonarQube Scan
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- name: SonarQube Scan
uses: sonarsource/sonarqube-scan-action@master
env:
SONAR_TOKEN: ${{ secrets.SONAR_TOKEN }}
SONAR_HOST_URL: ${{ secrets.SONAR_URL }}
with:
projectBaseDir: ./src
args: >
-Dsonar.projectName=$GITHUB_REPOSITORY
-Dsonar.projectKey=$SONAR_PROJECTKEY
-Dsonar.sourceEncoding=UTF-8
-Dsonar.language=js
C/C++/Objective-C용 Action yml 파일
CFamily의 경우 먼저 Build가 되어야한다
- Self-hosted Runner 사용 시
on:
push:
branches:
- "sonarscan"
paths:
- ".github/workflows/sonar.yml"
name: SonarQube
env:
SONAR_PROJECTKEY: cfamily
SONAR_CSCAN: /opt/build-wrapper
SONAR_SCAN: /opt/sonar-scan/
jobs:
sonarQubeTrigger:
name: SonarQube Scan
runs-on: [self-hosted, sonar]
steps:
- uses: actions/checkout@v3
- name: create property file
run: |
echo "sonar.host.url=${{ secrets.SONAR_URL }}" >> sonar-project.properties
echo "sonar.login=${{ secrets.SONAR_TOKEN }}" >> sonar-project.properties
echo "sonar.projectKey=$SONAR_PROJECTKEY" >> sonar-project.properties
echo "sonar.projectName=$GITHUB_REPOSITORY" >> sonar-project.properties
echo "sonar.sources=$GITHUB_WORKSPACE" >> sonar-project.properties
echo "sonar.cfamily.build-wrapper-output=${GITHUB_WORKSPACE}/build" >> sonar-project.properties
echo "sonar.sourceEncoding=UTF-8" >> sonar-project.properties
- name: build sonarqube
run: |
mkdir build
cmake -S . -B build
$SONAR_CSCAN/build-wrapper-linux-x86-64 --out-dir ${GITHUB_WORKSPACE}/build cmake --build build/ --config Release
- name: scanner start
run: $SONAR_SCAN/bin/sonar-scanner
- Github 제공 Runner 사용 시
on:
push:
branches:
- "sonarscan"
paths:
- ".github/workflows/sonar.yml"
name: SonarQube
env:
SONAR_PROJECTKEY: cFamily
jobs:
Sonarscan:
name: Build
runs-on: ubuntu-latest
env:
SONAR_SCANNER_VERSION: 4.7.0.2747
SONAR_SERVER_URL: ${{ secrets.SONAR_URL }}
BUILD_WRAPPER_OUT_DIR: sonar_build
SONAR_PROJECTKEY: cFamily
steps:
- uses: actions/checkout@v2
with:
fetch-depth: 0 # Shallow clones should be disabled for a better relevancy of analysis
- name: Set up JDK 11
uses: actions/setup-java@v1
with:
java-version: 11
- name: Download and set up sonar-scanner
env:
SONAR_SCANNER_DOWNLOAD_URL: https://binaries.sonarsource.com/Distribution/sonar-scanner-cli/sonar-scanner-cli-${{ env.SONAR_SCANNER_VERSION }}-linux.zip
run: |
mkdir -p $HOME/sonar
curl -sSLo "$HOME/sonar/sonar-scanner.zip" ${{ env.SONAR_SCANNER_DOWNLOAD_URL }}
unzip -o "$HOME/sonar/sonar-scanner.zip" -d $HOME/sonar/
echo "$HOME/sonar/sonar-scanner-${{ env.SONAR_SCANNER_VERSION }}-linux/bin" >> $GITHUB_PATH
- name: Download and set up build-wrapper
env:
BUILD_WRAPPER_DOWNLOAD_URL: ${{ env.SONAR_SERVER_URL }}/static/cpp/build-wrapper-linux-x86.zip
run: |
curl -sSLo $HOME/sonar/build-wrapper-linux-x86.zip ${{ env.BUILD_WRAPPER_DOWNLOAD_URL }}
unzip -o $HOME/sonar/build-wrapper-linux-x86.zip -d $HOME/sonar/
echo "$HOME/sonar/build-wrapper-linux-x86" >> $GITHUB_PATH
- name: create property file
run: |
echo "sonar.host.url=${{ secrets.SONAR_URL }}" >> sonar-project.properties
echo "sonar.login=${{ secrets.SONAR_TOKEN }}" >> sonar-project.properties
echo "sonar.projectKey=$SONAR_PROJECTKEY" >> sonar-project.properties
echo "sonar.projectName=$GITHUB_REPOSITORY" >> sonar-project.properties
echo "sonar.sources=$GITHUB_WORKSPACE" >> sonar-project.properties
echo "sonar.cfamily.build-wrapper-output=${GITHUB_WORKSPACE}/build" >> sonar-project.properties
echo "sonar.sourceEncoding=UTF-8" >> sonar-project.properties
- name: Run build-wrapper
run: |
mkdir ${{ env.BUILD_WRAPPER_OUT_DIR }}
cmake -S . -B ${{ env.BUILD_WRAPPER_OUT_DIR }}
build-wrapper-linux-x86-64 --out-dir ${{ env.BUILD_WRAPPER_OUT_DIR }} cmake --build build/ --config Release
- name: Run sonar-scanner
run: sonar-scanner
확인
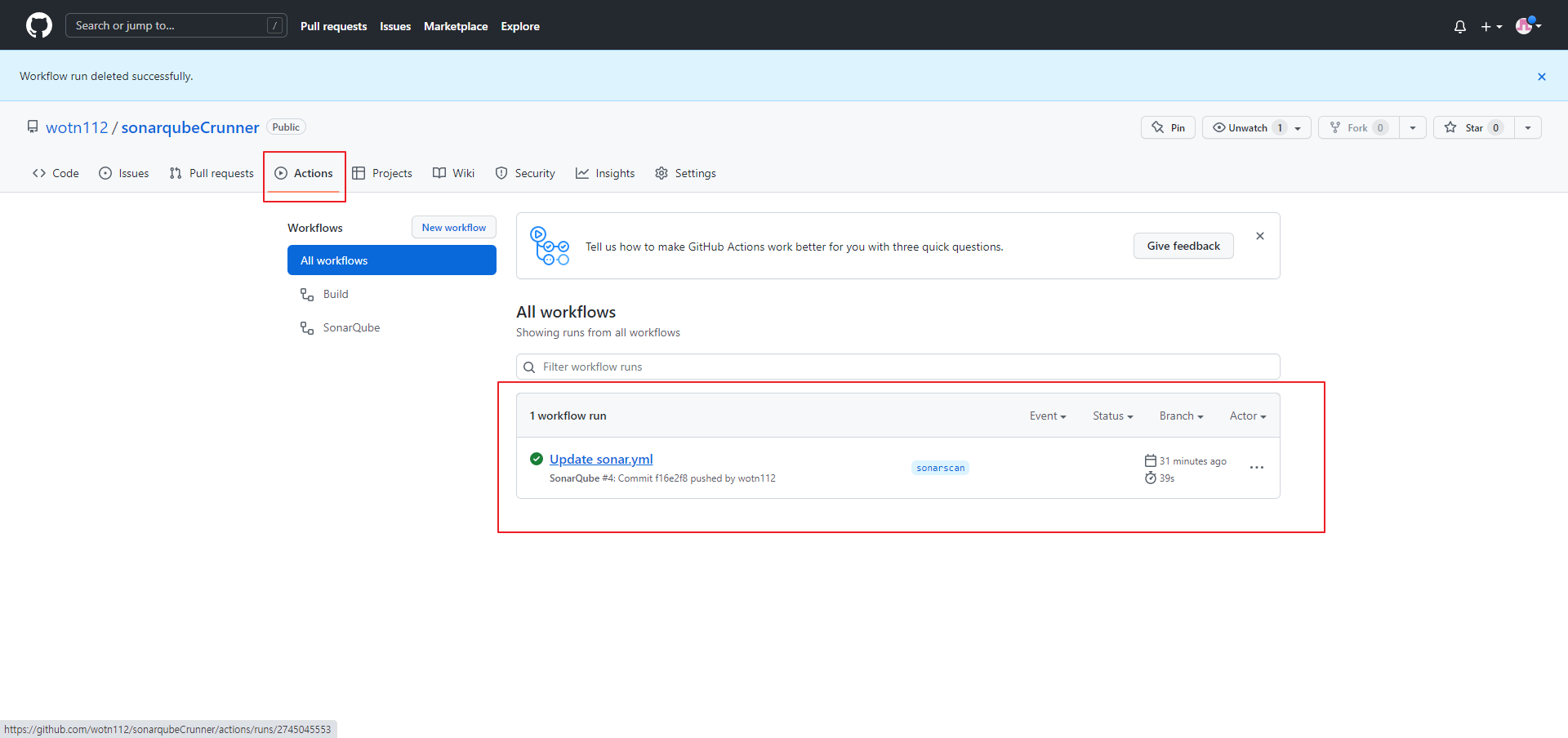
- Actions → All workflows 에 해당 작업의 성공여부를 확인 할 수 있다
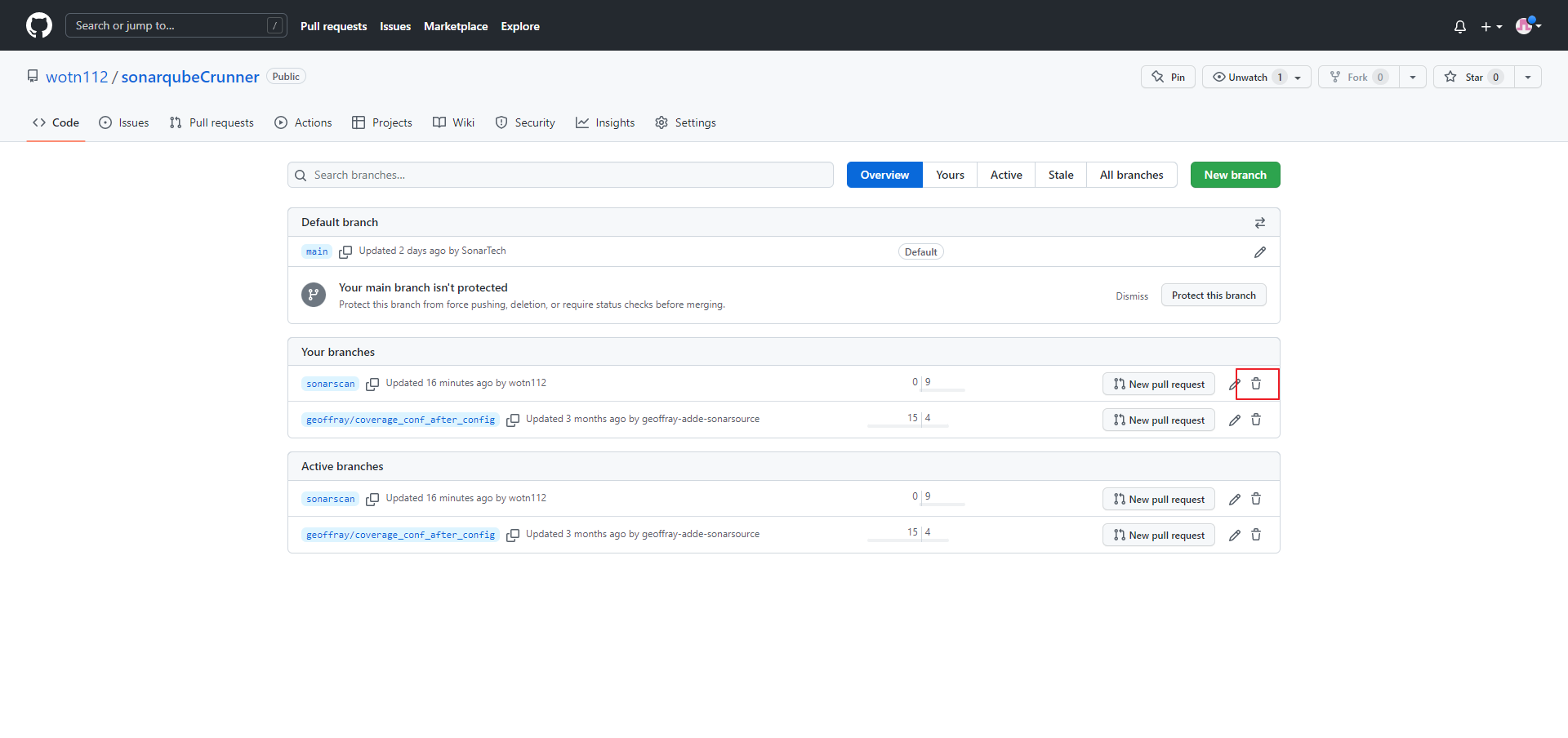
Branch 삭제
- 해당 작업을 완료한 후 해당 Branch를 삭제하고자 하는 경우
Branch 선택 → 삭제하고자 하는 Branch 오른쪽 휴지통 선택
참조 링크
Sonarqube
Github